How to Set up Automatic Updates on Ubuntu 18.04
Updated on
•4 min read

Regularly updating your Ubuntu system is one of the most important aspects of overall system security. If you don’t update your operating system’s packages with the latest security patches, you are leaving your machine vulnerable to attacks.
When managing multiple Ubuntu machines, manually updating the system packages may be time-consuming. Even if you manage a single system sometimes you may overlook an important update. This is where automatic unattended updates come handy.
In this tutorial, we will walk through how to configure automatic unattended updates on Ubuntu 18.04. The same steps apply for any Ubuntu-based distribution, including Kubuntu, Linux Mint, and Elementary OS.
Prerequisites
Before continuing with this tutorial, make sure you are logged in as a user with sudo privileges .
Installing the unattended-upgrades Package
The unattended-upgrades package includes tools that can automatically download and install updated packages.
Chances are that this package is already installed on your Ubuntu system.If not you can install it by entering the following command in your terminal:
sudo apt install unattended-upgradesOnce the installation is completed, the Unattended Upgrades service will start automatically. You can verify it by typing:
systemctl status unattended-upgrades● unattended-upgrades.service - Unattended Upgrades Shutdown
Loaded: loaded (/lib/systemd/system/unattended-upgrades.service; enab
Active: active (running) since Sun 2019-03-10 07:52:08 UTC; 2min 35s
Docs: man:unattended-upgrade(8)
CGroup: /system.slice/unattended-upgrades.service
Configuring Unattended Automatic Updates
The unattended-upgrades package can be configured by editing the /etc/apt/apt.conf.d/50unattended-upgrades file.
The default configuration should work fine for most users, but you can open the file and make changes as needed. You can update all packages or just security updates.
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}";
"${distro_id}:${distro_codename}-security";
// Extended Security Maintenance; doesn't necessarily exist for
// every release and this system may not have it installed, but if
// available, the policy for updates is such that unattended-upgrades
// should also install from here by default.
"${distro_id}ESM:${distro_codename}";
// "${distro_id}:${distro_codename}-updates";
// "${distro_id}:${distro_codename}-proposed";
// "${distro_id}:${distro_codename}-backports";
};
The first section defines what types of packages will be automatically updated. By default, it will install only the security updates, if you want to enable the updates from the other repositories you can uncomment the appropriate repository by removing the double slash // from the start of the line. Anything after // is a comment and it is not read by the package.
If for any reason you want to disable certain packages from being automatically updated simply add it to the package blacklist a package:
Unattended-Upgrade::Package-Blacklist {
// "vim";
// "libc6";
// "libc6-dev";
// "libc6-i686";
};
You may also want to receive an email if for some reason there is a problem with the automatic update. To do so uncomment the following two lines and enter your email address. Make sure that you have a tool that can send emails installed on your system, such as mailx or postfix
.
Unattended-Upgrade::Mail "your@email.com";
Unattended-Upgrade::MailOnlyOnError "true";
Enabling Unattended Automatic Updates
To enable automatic updated, you need to ensure that the apt configuration file /etc/apt/apt.conf.d/20auto-upgrades contains at least the following two lines, which should be included by default:
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";
The above configuration updates the package list, and installs available updates every day.
You can also add the following line that cleans the local download archive every 7 days.
APT::Periodic::AutocleanInterval "7";
Another way of enabling/disabling automatic updates is by running the following command, which will modify (or create if not exist) the /etc/apt/apt.conf.d/20auto-upgrades.
sudo dpkg-reconfigure -plow unattended-upgrades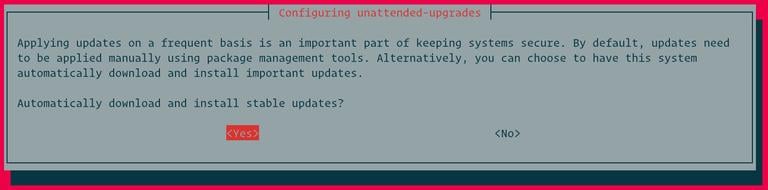
Testing
To test whether the auto-upgrades works perform a dry run:
sudo unattended-upgrades --dry-run --debugThe output should look something like this:
...
pkgs that look like they should be upgraded:
Fetched 0 B in 0s (0 B/s)
fetch.run() result: 0
blacklist: []
whitelist: []
No packages found that can be upgraded unattended and no pending auto-removals
The history of the automatic unattended-upgrades is logged in the /var/log/unattended-upgrades/unattended-upgrades.log file.
Conclusion
In this tutorial, you have learned how to configure automatic unattended updates and keep your system up-to-date.
If you have any questions or feedback, feel free to leave a comment.


