How to Set Up a Firewall with UFW on Ubuntu 20.04
Updated on
•8 min read

A firewall is a tool for monitoring and filtering incoming and outgoing network traffic. It works by defining a set of security rules that determine whether to allow or block specific traffic.
Ubuntu ships with a firewall configuration tool called UFW (Uncomplicated Firewall). It is a user-friendly front-end for managing iptables firewall rules. Its main goal is to make managing firewall easier or, as the name says, uncomplicated.
This article describes how to use the UFW tool to configure and manage a firewall on Ubuntu 20.04. A properly configured firewall is one of the most important aspects of overall system security.
Prerequisites
Only root or users with sudo privileges can manage the system firewall. The best practice is to run administrative tasks as a sudo user.
Install UFW
UFW is part of the standard Ubuntu 20.04 installation and should be present on your system. If for some reason it is not installed, you can install the package by typing:
sudo apt updatesudo apt install ufw
Check UFW Status
UFW is disabled by default. You can check the status of the UFW service with the following command:
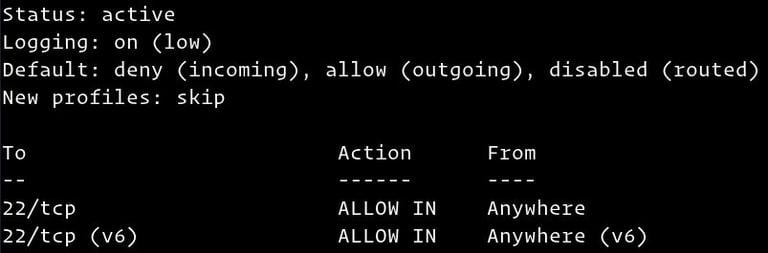
sudo ufw status verboseThe output will show that the firewall status is inactive:
Status: inactiveIf UFW is activated, the output will look something to the following:
UFW Default Policies
The default behavior of the UFW Firewall is to block all incoming and forwarding traffic and allow all outbound traffic. This means that anyone trying to access your server will not be able to connect unless you specifically open the port. Applications and services running on your server will be able to access the outside world.
The default polices are defined in the /etc/default/ufw file and can be changed either by manually modifying the file or with the sudo ufw default <policy> <chain> command.
Firewall policies are the foundation for building more complex and user-defined rules. Generally, the initial UFW Default Policies are a good starting point.
Application Profiles
An application profile is a text file in INI format that describes the service and contains firewall rules for the service. Application profiles are created in the /etc/ufw/applications.d directory during the installation of the package.
You can list all application profiles available on your server by typing:
sudo ufw app listDepending on the packages installed on your system, the output will look similar to the following:
Available applications:
Nginx Full
Nginx HTTP
Nginx HTTPS
OpenSSHTo find more information about a specific profile and included rules, use the following command:
sudo ufw app info 'Nginx Full'The output shows that the ‘Nginx Full’ profile opens ports 80 and 443.
Profile: Nginx Full
Title: Web Server (Nginx, HTTP + HTTPS)
Description: Small, but very powerful and efficient web server
Ports:
80,443/tcpYou can also create custom profiles for your applications.
Enabling UFW
If you’re connecting to your Ubuntu from a remote location, before enabling the UFW firewall, you must explicitly allow incoming SSH connections. Otherwise, you will no longer be able to connect to the machine.
To configure your UFW firewall to allow incoming SSH connections, type the following command:
sudo ufw allow sshRules updated
Rules updated (v6)If SSH is running on a non-standard port , you need to open that port.
For example, if your ssh daemon listens on port 7722, enter the following command to allow connections on that port:
sudo ufw allow 7722/tcpNow that the firewall is configured to allow incoming SSH connections, you can enable it by typing:
sudo ufw enableCommand may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall is active and enabled on system startupYou will be warned that enabling the firewall may disrupt existing ssh connections, just type y and hit Enter.
Opening Ports
Depending on the applications that run on the system, you may also need to open other ports. The general syntax to open a port is as follows:
ufw allow port_number/protocolBelow are a few ways on how to allow HTTP connections.
The first option is to use the service name. UFW checks the /etc/services file for the port and protocol of the specified service:
sudo ufw allow httpYou can also specify the port number, and the protocol:
sudo ufw allow 80/tcpWhen no protocol is given, UFW creates rules for both tcp and udp.
Another option is to use the application profile; in this case, ‘Nginx HTTP’:
sudo ufw allow 'Nginx HTTP'UFW also support another syntax for specifying the protocol using the proto keyword:
sudo ufw allow proto tcp to any port 80Port Ranges
UFW also allows you to open port ranges. The start and the end ports are separated by a colon (:), and you must specify the protocol, either tcp or udp.
For example, if you want to allow ports from 7100 to 7200 on both tcp and udp, you would run the following command:
sudo ufw allow 7100:7200/tcpsudo ufw allow 7100:7200/udp
Specific IP Address and port
To allow connections on all ports from a given source IP, use the from keyword followed by the source address.
Here is an example of whitelisting an IP address:
sudo ufw allow from 64.63.62.61If you want to allow the given IP address access only to a specific port, use the to any port keyword followed by the port number.
For example, to allow access on port 22 from a machine with IP address of 64.63.62.61, enter:
sudo ufw allow from 64.63.62.61 to any port 22Subnets
The syntax for allowing connections to a subnet of IP addresses is the same as when using a single IP address. The only difference is that you need to specify the netmask.
Below is an example showing how to allow access for IP addresses ranging from 192.168.1.1 to 192.168.1.254 to port 3360 (MySQL
):
sudo ufw allow from 192.168.1.0/24 to any port 3306Specific Network Interface
To allow connections on a particular network interface, use the in on keyword followed by the name of the network interface:
sudo ufw allow in on eth2 to any port 3306Denying connections
The default policy for all incoming connections is set to deny, and if you haven’t changed it, UFW will block all incoming connections unless you specifically open the connection.
Writing deny rules is the same as writing allow rules; you only need to use the deny keyword instead of allow.
Let’s say you opened ports 80 and 443, and your server is under attack from the 23.24.25.0/24 network. To deny all connections from 23.24.25.0/24 you would run the following command:
sudo ufw deny from 23.24.25.0/24Here is an example of denying access only to ports 80 and 443 from 23.24.25.0/24 you can use the following command:
sudo ufw deny proto tcp from 23.24.25.0/24 to any port 80,443Deleting UFW Rules
There are two different ways to delete UFW rules by rule number, and by specifying the actual rule.
Deleting rules by rule number is easier, especially when you are new to UFW. To delete a rule by a rule number first, you need to find the number of the rule you want to delete. To get a list of numbered rules, use the ufw status numbered command:
sudo ufw status numberedStatus: active
To Action From
-- ------ ----
[ 1] 22/tcp ALLOW IN Anywhere
[ 2] 80/tcp ALLOW IN Anywhere
[ 3] 8080/tcp ALLOW IN AnywhereTo delete rule number 3, the one that allows connections to port 8080, you would enter:
sudo ufw delete 3The second method is to delete a rule by specifying the actual rule. For example, if you added a rule to open port 8069 you can delete it with:
sudo ufw delete allow 8069Disabling UFW
If for any reason you want to stop UFW and deactivate all the rules, you can use:
sudo ufw disableLater if you want to re-enable UTF and activate all rules, just type:
sudo ufw enableResetting UFW
Resetting UFW will disable UFW, and delete all active rules. This is helpful if you want to revert all of your changes and start fresh.
To reset UFW, type in the following command:
sudo ufw resetIP Masquerading
IP Masquerading is a variant of NAT (network address translation) in the Linux kernel that translates the network traffic by re-writing the source and destination IP addresses and ports. With IP Masquerading, you can allow one or more machines in a private network to communicate with the Internet using one Linux machine that acts as a gateway.
Configuring IP Masquerading with UFW involves several steps.
First, you need to enable IP forwarding. To do that, open the /etc/ufw/sysctl.conf file:
sudo nano /etc/ufw/sysctl.confFind and uncomment the line which reads net.ipv4.ip_forward = 1:
net/ipv4/ip_forward=1Next, you need to configure UFW to allow forwarded packets. Open the UFW configuration file:
sudo nano /etc/default/ufwLocate the DEFAULT_FORWARD_POLICY key, and change the value from DROP to ACCEPT:
DEFAULT_FORWARD_POLICY="ACCEPT"Now you need to set the default policy for the POSTROUTING chain in the nat table and the masquerade rule. To do so, open the /etc/ufw/before.rules file and append the lines highlighted in yellow, as shown below:
sudo nano /etc/ufw/before.rulesAppend the following lines:
#NAT table rules
*nat
:POSTROUTING ACCEPT [0:0]
# Forward traffic through eth0 - Change to public network interface
-A POSTROUTING -s 10.8.0.0/16 -o eth0 -j MASQUERADE
# don't delete the 'COMMIT' line or these rules won't be processed
COMMITDon’t forget to replace eth0 in the -A POSTROUTING line to match the name of the public network interface:
When you are done, save and close the file.
Finally, reload the UFW rules by disabling and re-enabling UFW:
sudo ufw disablesudo ufw enable
Conclusion
We’ve shown you how to install and configure a UFW firewall on your Ubuntu 20.04 server. Be sure to allow all incoming connections that are necessary for the proper functioning of your system while limiting all unnecessary connections.
For more information on this topic, visit the UFW man page .
If you have questions, feel free to leave a comment below.


