How to Set Up SSH Keys on CentOS 7
Updated on
•4 min read

Secure Shell (SSH) is a cryptographic network protocol designed for a secure connection between a client and a server.
The two most popular SSH authentication mechanisms are password based authentication and public-key based authentication. Using SSH keys is generally more secure and convenient than traditional password authentication.
This tutorial explains how to generate SSH keys on CentOS 7 systems. We will also show you how to set up an SSH key-based authentication and connect to your remote Linux servers without entering a password.
Creating SSH keys on CentOS
Before generating a new SSH key pair, it is a good idea to check for existing SSH keys on your CentOS client machine.
To do so, run the following ls command that lists all public keys if there are any:
ls -l ~/.ssh/id_*.pubIf the output of the command returns something like No such file or directory or no matches found it means that you don’t have SSH keys on your client machine, and you can proceed with the next step and generate SSH key pair.
If there are existing keys, you can either use those and skip the next step or backup up the old keys and generate new ones.
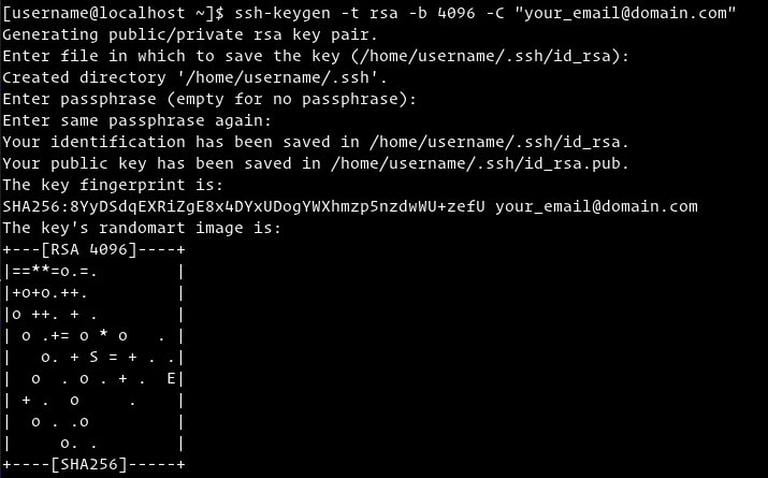
Start by generating a new 4096 bits SSH key pair with your email address as a comment:
ssh-keygen -t rsa -b 4096 -C "your_email@domain.com"You will be prompted to specify the file name:
Enter file in which to save the key (/home/yourusername/.ssh/id_rsa):
Press Enter to accept the default file location and file name.
Next, you’ll be asked to type a secure passphrase. Whether you want to use a passphrase, it’s up to you. If you choose to use a passphrase, you will get an extra layer of security.
Enter passphrase (empty for no passphrase):
If you don’t want to use a passphrase just press Enter.
The whole interaction looks like this:
To verify your new SSH key pair is generated, type:
ls ~/.ssh/id_*/home/yourusername/.ssh/id_rsa /home/yourusername/.ssh/id_rsa.pub
Copy the Public Key to CentOS Server
Now that the SSH key pair is generated, the next step is to copy the public key to the server you want to manage.
The easiest and the recommended way to copy the public key to the remote server is by using a utility called ssh-copy-id. On your local machine terminal type:
ssh-copy-id remote_username@server_ip_addressYou will be prompted to enter the remote_username password:
remote_username@server_ip_address's password:
Type the password, and once the user is authenticated, the public key ~/.ssh/id_rsa.pub will be appended to the remote user ~/.ssh/authorized_keys file. The connection will be closed.
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'username@server_ip_address'"
and check to make sure that only the key(s) you wanted were added.
If the ssh-copy-id utility is not available on your local computer, use the following command to copy the public key:
cat ~/.ssh/id_rsa.pub | ssh remote_username@server_ip_address "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys && chmod 600 ~/.ssh/authorized_keys"Login to your server using SSH keys
After completing the steps above, you should be able to log in to the remote server without being prompted for a password.
To verify it, try to login to your server via SSH :
ssh remote_username@server_ip_addressIf you haven’t set a passphrase for the private key, you will be logged in immediately. Otherwise, you will be asked to enter the passphrase.
Disabling SSH Password Authentication
To add an additional layer of security to your remote server, you can disable SSH password authentication.
Before continuing, make sure you can log in to your server without a password as a user with sudo privileges .
Follow the steps below to disable SSH password authentication:
Log into your remote server:
ssh sudo_user@server_ip_addressOpen the SSH configuration file
/etc/ssh/sshd_configwith your text editor :sudo nano /etc/ssh/sshd_configSearch for the following directives and modify as it follows:
/etc/ssh/sshd_configPasswordAuthentication no ChallengeResponseAuthentication no UsePAM noOnce you are done save the file and restart the SSH service by typing:
sudo systemctl restart ssh
At this point, the password-based authentication is disabled.
Conclusion
In this tutorial, you have learned how to generate a new SSH key pair and set up an SSH key-based authentication. You can add the same key to multiple remote servers.
We have also shown you how to disable SSH password authentication and add an additional layer of security to your server.
By default, SSH listens on port 22. Changing the default SSH port reducess the risk of automated attacks.
If you are regularly connecting to multiple systems, you can simplify your workflow by defining all of your connections in the SSH config file .
If you have any questions or feedback, feel free to leave a comment.